- Test Password Strength
- Integrity Checker
- Simple Malware Scanner Using Yara
- Keylogging (Spyware)
- Hashed Password Cracker
- Simple Vulnerability Matcher
- Non-hashed Password Cracker

Test Password Strength
The password strength project aims to develop a password-strength testing tool. It will provide users with an easy and efficient way to evaluate the strength of their passwords. The tool will analyze various factors such as length, complexity, and inclusion of special characters to determine the strength level. Additionally, it will provide suggestions and tips forcreating stronger passwords.


The project will focus on creating a user-friendly interface as a web / Desktop application and incorporating robust algorithms to assess password strength accurately. Ultimately, the goal is to enhance cybersecurity awareness and empower users to protect their accounts with strong passwords.
Integrity Checker
The Integrity Checker aims to provide security for operating systems. The tool will ensure the integrity and security of system files by verifying their integrity against known hashes or checksums. It will regularly scan the operating system files and compare them with a trusted database to detect any unauthorized modifications or tampering. The integrity checker will provide real-time alerts and notifications for any discrepancies found, enabling administrators or users to take immediate action.

Simple Malware Scanner Using Yara
The project aims to create a simple malware scanner utilizing the Yara framework. The tool will scan files and directories using Yara rulesets containing known malware patterns and signatures. The scanner will compare the patterns in the rulesets with the content of the files, allowing for the detection of malicious files and potentially harmful software.
It will provide users with real-time notifications and reports on the presence of any identified malware. The project aims to offer a user-friendly and efficient solution for detecting and mitigating malware threats using the power of Yara’s pattern-matching capabilities.
Hashed Password Cracker

The hashed password cracker tool will be designed to crack hashed passwords often used for secure storage and authentication. It will utilize various techniques such as brute force, dictionary attacks, and rainbow table lookups to attempt to reverse-engineer the original password from its hash value.The cracker will provide a user-friendly interface for inputting hashed passwords and will employ advanced algorithms and optimization techniques to increase efficiency and speed. The project aims to assist users in recovering forgotten passwords or testing the strength of their hashed password implementations.
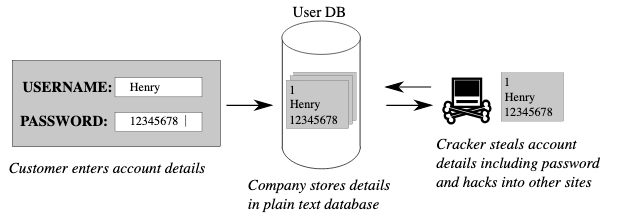
Non-hashed Password Cracker
The simple non-hashed password cracker tool will focus on cracking passwords stored in plaintext or weakly encrypted formats. It will utilize various techniques such as brute force, dictionary attacks, and pattern matching to attempt to reveal the original passwords. The cracker will provide a user-friendly interface for inputting password files or encrypted data and will employ efficient algorithms to optimize the cracking process
Keylogging (Spyware)

In computing, a keylogger is a piece of software that monitors all the keystrokes that take place on a computer’s keyboard. It monitors previously pressed and currently active keys to record user activity. You can consider the following project on the concept of keylogging:
- Create a script that can record keystrokes.
- Create and bind a keylogger with legitimate application/software to record user activity, basically spyware.
- Create a script that can detect the presence of a keylogger on endpoint.
